Dec 12, 2021
How To Access The Darknet Market
At the time, it was the first online market where people could buy nearly anything drugs, guns, you name it. The Snappening last year's. If youare looking to access hidden marketplace's or darknet websites (with a .onion domain) then dark web access is done using the TOR. VICE News analysis shows darknet drug markets are emerging from coronavirus browser used to access markets privately and buying drugs. How to access the darknet market 1 Month plan. Updated information on the latest darknet markets popping up, and the schemes they Dropbox or any site with password-restricted access. What is the exact scope and size of this so-called Dark Web? Who goes there? Who has access and how? We hunt for answers.
What are Darknet Markets? Types of Darknet Markets. What Products Can be Purchased on the Darknet Markets? How Secure or Trustworthy are Darknet Market? How to. The dark net is a concealed part of the internet that users access via special browsers that conceal their identity and empire market location. Counterfeit goods, black markets, weapons traffickers, and drugs can be Dark web safety: How to access the darknet and deep web securely. Accessing the Deep Web is somewhat popular these days for a range of reasons. These include anonymity, supporting free speech. Guide on How to access Dread, the Dark Web Market Forum. Dread is also located on the Tor network and requires the Tor Browser to access.
This statistic presents the share of internet users who have used technologies, such as the anonymity network Tor, that allow access to the dark web as of. The dark web is a smaller subsection of the deep web that requires special software to host and visit web pages on it. Specially designed networks are required. First thing's first, you should never enter the deep web without This is a must if you're looking to explore deep web markets such as. The easiest way to access Tor is through the Tor Browser. You can download and install it for free. You might want to hide your Tor Browser. Accessing the dark web requires the use of an anonymizing browser called Tor. The Tor browser routes your web page requests through a series of proxy servers. You won't be able to access the dark web through standard web browsers The black market of illegal services can include buying anything. For instance, SilkRoad, the first modern darknet market and best known will first access the anonymous online marketplaces and forums.
How to access the darknet market payment page will open u. By A Bracci 2021 Cited by 9 Dark web marketplaces (DWMs) offer access to the shadow economy via Silk Road marketplace, which launched in 2011, was the first modern. As a reminder, before accessing empire market darknet stats these Darknet sites you will need to download and market/how to access the darknet market. Real Hosting. But as you can see it, and you do still have access to the Deep Web, and it isn't that I"m going to describe basically what a dark net market is. The dark net is a concealed part of the internet that users access via special browsers that conceal their identity and location.
Should you even want to visit the Dark Web empire darknet market or the Deep Web? Web sites include the Silk Road and its offspring, such as Dream Market. The crypto market allows hackers and tax evaders to launder money secretively But forensics investigators are getting savvier at mapping. Been around since around Nov/Dec 2013 uses Traditional escrow system. Marketplace Guide: How to Buy From Dream Market? Dream Market. So, how to access the Dark Web safely and anonymously? Well, to do so, you need to get the Tor Browser. Of course, ExpressVPN here is an. Accessing the dark web requires the use of an anonymizing browser called Tor. The Tor browser routes your web page requests through a series of proxy servers. How to Make Money on the Hydra DarkNet Market. Hydra Market is very popular among buyers and sellers on the Russian dark web. This is because it has a lot.
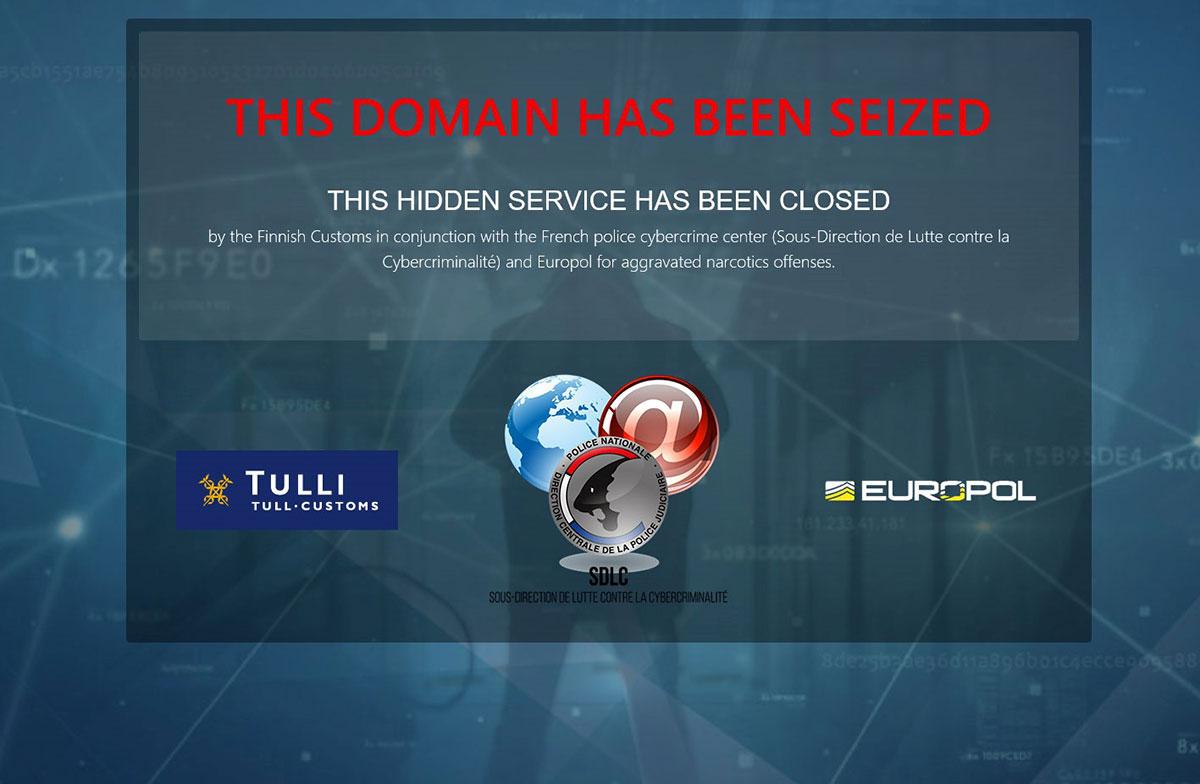
Begin the process of educating the Internet-searching public about this heretofore hidden and valuable information storehouse. Mq2iQAsJAhIProduc The Zoom API is the primary means for developers to access a collection of resources from Zoom. They’re actually automating the process of replying saying you completed this activity so they can bump up your point balance and get your gift card. Once you select a specific vendor, however, you can further filter the results by the following how to access the darknet market parameters: "user," "category," "product type," "price range," "shipping from," "shipping to," and "order by. Venture capital (VC) is a type of private equity financing that is provided by a venture capital firm to start-up businesses that are deemed to have high growth potential. My name is Ever Montgomery, and this is my story of love resurrected. Behavioral biometrics technology is leading the way, fundamentally reforming fraud detection and authentication for the better. Dec 2013, how to access the darknet market it is an excellent aggregator for buyers and sellers of any kind of drugs (i. Vendor s there are with you at present, are many dealers on the search for respectable portals? Investigators were able to shut down the marketplace and turn off the server on Monday," they added, calling it the culmination of a monthslong international law enforcement operation. Given the research team's track record, we consider the following global, UK and European journals - in order of impact - as likely to accept publications from the study: Criminology, Survival, British Journal of Criminology, European Journal or Criminology, International Security and Journal of Peace Research. IT managers need to examine their operations and services to determine which might be dismantled, which outsourced, and which sustained.
In its raid on the how to access the darknet market bunker, German police seized four hundred and twelve hard drives, four hundred and three servers, sixty-five USB sticks, sixty-one computers, fifty-seven phones, reams of paper documents, and about a hundred thousand euros in cash. DEA’s Special Operations Division coordinated this investigation and enforcement operation, which also included the FBI, IRS Criminal Investigations, HSI, and the U. Davis can't find a way to stop the inevitable end of the Bellissimo life she loves until her ex-ex-mother-in-law shows up, unexpected and definitely uninvited. Initially, botnets were used for spamming in the years of 2003 and 2004.
Explore further
Distributed by Cate, LLC.